Is Your CPU Spying On You?
Let me ask you this!
What if I tell you that there is a special chip in your computer that has absolute control over your entire system, is remotely accessible, has secret but propitiatory code that you can’t look at. There is no way to disable it.
Well it’s real, and it’s pretty scary
Let me introduce you to the two things you never heard before
1. Intel Management Engine (IME)
And
2. AMD Platform Security Processor
 |
| This is just an example not an actual photo |
Like I just said, these are essentially backdoor in almost every computer that has been made in the past ten years and so. Intel and AMD swear up and down, and they are only used for legitimate purposes so that we have no choice to take their words as truth.
First, let’s talk about what these are, starting with the Intel Management Engine.
It’s a separate, standalone co-processor that is physically imbibed in every Intel chipset. To put it, it’s like a mini-computer within your computer. But the scary thing about it is that no one knows precisely what it does because it has got propitiatory code, and Intel has not released that source code.
Now obviously, it has legitimate features that Intel has no problem talking about, but you can’t help but wonder if there is a little more to it. Here is a list of things that this hardware can do.
1. Direct RAM access:- It has access to all your computer’s RAM, completely bypassing the main
CPU
2. All Peripherals:- It has access to everything attached to your computer, every peripheral.
3. Network Interface:- It has access to your network interface.
4. Bypass OS ultimately:- It has complete access to your OS firewall system
5. Works when your PC is off:- It can turn your PC on and off remotely
So, there is no surprise that it can access these things even when your computer turned off.
By now, you might be thinking, “What the hell,” why is it even exists? Why is this chip has access to everything? Why can’t I disable it?
Well, it’s the main purpose to allow you or a company system administrator to remotely monitor, maintain update or repair your computer. So now, you might also think, “Okay! That makes sense, but I don’t need any of that; this is my personal computer, so how do I disable it?
Well, I have got a piece of bad news for you, “You can’t.”
And you can’t buy Intel core processor without one and as I mentioned it before you can’t even escape it by going with an AMD processor because they have their own version of it named Platform Security Processor (PSP). And it’s a different implementation but for the purpose of this post it’s is just close enough to Intel Management Engine as it can also control everything in your computer and we have no idea what it’s actual code is.
The next thing you guys will probably say “Okay, so now my computer has a secret backdoor; great! but at least my cell phone does not use AMD or Intel, so surely I am safe.”
WRONG!
Have you ever heard about a Baseband Processor? Probably not. Every cell phone has one, and its purpose is to convert between digital signals and radio signals for the telephone to the antenna.
So, you need one of these for your phone even to work, and yes, this one also has low-level access to all sorts of data on your phone, but the essential thing to note about it is just like Intel ME and AMD PSP, Baseband processors are all per propitiatory.
So, no matter what manufacturer makes the phone, they all have their version of this ‘Black box processor’ that can’t be accessed but can control your device.
Well yes, it’s doubtful that Intel and AMD are using this to spy on people almost, definitely not. Because they have little to gain and everything to lose if they ever get caught spying.
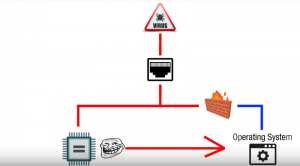
So it’s not Intel or AMD that we need to worry about. But the real problem is the possibility that these individual chips could be cracked by some hacker group or more likely some government, while these chips are obviously protected with some hardcore encryption but that’s doesn’t mean that someone couldn’t discover some very smart exploits for it. And if that happens, they will potentially be able to take control of literally any computer they wanted, remotely.
And no one would ever know because they can’t see inside the chip in the first place so they can’t say that it was exploited and on the top of that, because it bypasses the central processor altogether there is no way to stop it, and you wouldn’t even know it’s doing anything. And I don’t even think that you will be able to defend against this kind of attack. If you think about it, this thing has dedicated access to your network interface, so if an attacker wants to send you a malicious payload to your computer, even it will get blocked by your firewall, it might still go directly to the Blackbox chip and infect your OS.
Okay! So here I end this topic. I hope this post didn’t freak you out too much.
If you have any questions related to this post or want me to post on a particular topic, let me know in the comment box and do make sure to share the post with your friends.

Leave a Reply